Disclaimer: In Real Life is a platform for everyday people to share their experiences and voices. All articles are personal stories and do not necessarily echo In Real Life’s sentiments.
This particular anonymous local hacker from KL comes from an extensive business and cybersecurity background. He has over 10 years of experience breaking and securing IT systems, over half of which as a security consultant delivering projects related to cybersecurity strategy, identity and access management, and security testing. Of course, this was before starting his career as a freelancer.
His rare combination of exemplary business know-how and adept cybersecurity strategy execution is what has made his career take off. When he’s away from bug bounty hunting, security training and tests, he can be found composing music and playing the piano.
Today, he shares with IRL his journey and together we explore some of the technicalities in the hacking world. Heads up, loads of jargon ahead!

How did you come up with your [redacted] username?
It’s a handle that I originally chose because it sounded fun but didn’t mean anything. Recently, however, I found out it appears to be the name of some Belgian pastry.
How did you discover hacking?
I am of the generation of kids that learned to write code on calculators in school, which sparked my interest in computer programming. However, I remember classmates popping XSS alerts in online school forums years before I learned what they were. My skills developed slowly over years of learning visual basic, HTML and JavaScript, until I learned how to employ those skills against websites (which, in the 2000s, were a lot less secure than they are today).
By the end of secondary school, my interests were sufficiently solidified to pursue a degree in computer science, where I learned more about software security and hacking. I eventually landed my first job in cyber security where I was further trained as a penetration tester.
What motivates you to hack and why do you hack through bug bounties (compensation for reporting bugs in security exploitation)?
There is nothing like the thrill of exploiting a cool vulnerability! I mean that quite literally: the adrenaline rush that some people go bungee jumping for, I try to achieve by spending my time looking for fun bugs.
There’s also a lot of satisfaction in being the first to find holes in production systems. The added bonus of knowing you’ve upped an organization’s security game… The bounties are a very welcome icing on the cake.

What makes a programme an exciting target?
Wildcard scopes (e.g. *.example.com) always get me excited. Not because my recon is great, but because there’s a better chance of coming across interesting applications. It shows an organisation is committed to security across all their assets, which to me is a sign of maturity, and sets an expectation for the way in which reports will be handled.
I also like a target that contains a wide variety of complex features, increasing the chances of finding a fun combination of vulnerabilities. If a programme incites creativity, I’m going to be hooked.
What keeps you engaged in a programme and what makes you disengage?
I love when a programme is quick to acknowledge a bug report, when a report sparks an interesting discussion or conversation about impact, and when a programme awards a bounty on triage. Something that will definitely keep me engaged is when I am encouraged to keep digging on a vulnerability, and see how far I can take it.
On the other hand, I tend to stay away from a programme when reports are left without a response for multiple days, or when my suggested impact rating is lowered without further comment or discussion.
How many programmes do you focus on at once? Why?

Typically I will be drawn back to programmes where I’ve had some earlier success, which means I’m usually focusing on the same four or five targets. Except I deviate from this when I receive a fresh invite, in which case I will likely spend a bit of time to see if there’s something to spark my interest.
In general, I don’t feel like I do a great job of managing my attention, so I’ll often get too involved in a programme that’s hardly worth the time, or get immediately sidetracked and hop from programme to programme without finding anything for days or weeks.
What do you wish every company knew before starting a bug bounty programme?
Be prepared to enable easy access to your applications. If you have geolocation restrictions in place, don’t expect hackers to spend hours circumventing those. I’ve been invited into programmes that require registration with a US SSN in the past, or greet me with: “The owner of this website has banned the country or region your IP address is in from accessing this website”.
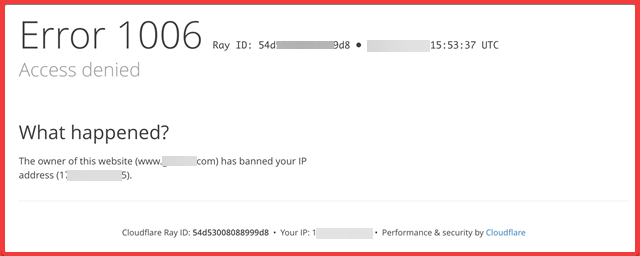
Similarly, if I need credentials to log in, don’t wait 15 days to provision them. I realize I may not be the world’s most patient person, but I imagine those situations are going to lead to a hard pass from more hackers than just me.
How do you see the bug bounty space evolving over the next 5-10 years?
Based on the changes it underwent in the last five years, I expect it to continue growing and attracting the next generation of talented people from around the world to put their skills to the test. I also wouldn’t be surprised to see it spread into industries that are currently less likely to solicit the help of hackers.
I hope we will also see an evolution in the way bug bounties can help increase the security of organisations that cannot afford to pay bounties but would still benefit from responsible disclosure of security bugs.
How do you see the future of collaboration on hacking platforms evolving?
My best experience with collaboration was during live hacking events which I have personally attended overseas. Either that or just joining a bunch of hacking groups online, where everybody is continuously sharing information and being uplifted by each other’s knowledge. To maintain or recreate that feeling of shared effort and rewards away from a live event would be amazing.
I can only see that happening with tools and platforms that enable shared notes taking, commenting, etc., which are currently reserved for people who set up their own collaboration spaces.
What educational hacking resources do you wish existed that don’t exist today?
This is hard to say. There is such an enormous wealth of amazing resources that I really can’t think of something that’s missing.
What advice would you give to the next generation of hackers?
Be patient but persistent.
For more stories like this, read: Malaysians Keep Getting Their Bank Accounts Hacked – Here Are The Best Ways To Prevent It and What I Learned About Cyber Security After My Mother’s Facebook Account Was Hacked
You might also like
More from Real Skills
How I Saved Almost RM50,000 On Buying My First Car
Here's how this Malaysian man with a RM3,500 salary saved RM50,000 on his first car.
Angry M’sian Boss Demands Unpaid Overtime Over Raya, Causes 9 Staff To Quit
An anonymous employee at a local SME shares how a bad-tempered boss eventually caused 9 staff to quit before Hari …
I Studied In Chinese School As A Malay Boy, Here’s What I Learnt
Every time I used Mandarin outside of school, family members would come up to me at gatherings and ask me …